 Hackers are growing bolder by the day, taking on huge organizations like the IRS and Sony Entertainment, and forcing businesses to stay on the defensive at all times. In spite of this, what can the average small business do to keep themselves safe? For starters, you can integrate multi-factor authentication, a solution designed to make it extra difficult for hackers to access online accounts.
Hackers are growing bolder by the day, taking on huge organizations like the IRS and Sony Entertainment, and forcing businesses to stay on the defensive at all times. In spite of this, what can the average small business do to keep themselves safe? For starters, you can integrate multi-factor authentication, a solution designed to make it extra difficult for hackers to access online accounts.
Better yet, it’s super easy to setup multi-factor authentication of your Office 365 account, and all accounts associated with your company. Follow these steps and you’ll be done before you know it.
First, you’ll want to log into the Office 365 Portal with your administrator credentials. Then, click on the users and groups tab.
From here, go to the Setup link, located to the right of Set Multi-factor authentication requirements.
This will show a display featuring all of the usernames associated with your Office 365 account. Select the box to the left of the user that you’ll be applying multi-factor authentication to. Then, go to the information box to the right of the user and select Enable, located under quick steps.
A box should open called About enabling multi-factor auth. Make sure you check out these links if you need more information concerning multi-factor authentication. When you’re ready to proceed, all you have to do is click enable multi-factor auth.
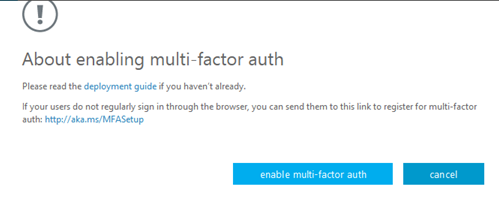 Office 365 will inform you that your settings have been applied. You can click close to end the process.
Office 365 will inform you that your settings have been applied. You can click close to end the process.
Now that you’ve finished the setup process for multi-factor authentication in the administrator settings, users will be asked to make certain changes to their accounts the next time they log in. After the initial login process, a user will need to verify their identity and set up multi-factor authentication on the user-end.
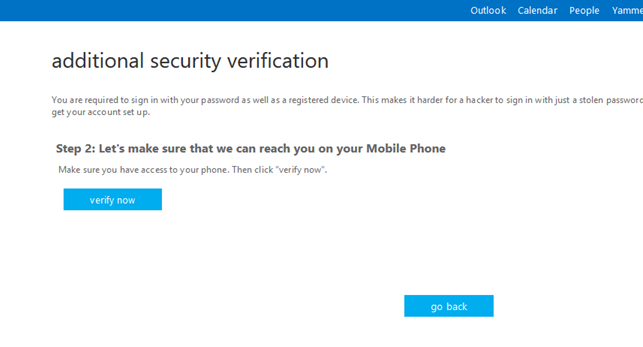
The user will be required to select which MFA method they prefer, like their mobile phone number, so they can receive a call or SMS messages from Microsoft. After entering the preferred phone number, click verify.
Next, Microsoft will contact your phone with a unique code that you will enter in order to verify the number. Depending on if you’re using a browser-based MFA setup, you may be asked to change your password too (it’s a best practice to regularly adopt new passwords).
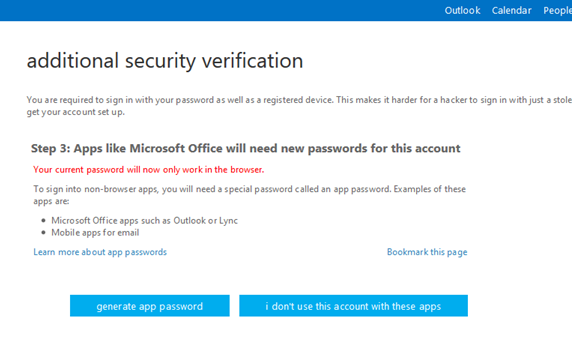
After creating and implementing a new password, multi-factor authentication will be set up for all the Office 365 accounts that you desire to have an extra layer of protection for.
For more information about multi-factor authentication, and how you can take advantage of similar services for all of your online accounts, give Voyage Technology a call at 800.618.9844.


