 One of the most unpleasant aspects regarding email is the anxiety associated with sending an important message. Did the message really send? Has the recipient read it yet? Should I contact them and ask if they got my email? The struggle is real. Thankfully, there’s a Chrome extension designed to alleviate this stress by answering these pressing questions.
One of the most unpleasant aspects regarding email is the anxiety associated with sending an important message. Did the message really send? Has the recipient read it yet? Should I contact them and ask if they got my email? The struggle is real. Thankfully, there’s a Chrome extension designed to alleviate this stress by answering these pressing questions.
Actually, there are a variety of tools that will tell you if a sent email’s been read or not; but for now, we want to share with you MailTrack, a free solution for Gmail. Check out MailTrack’s website and download it from Chrome’s webstore: http://mailtrack.io/en/
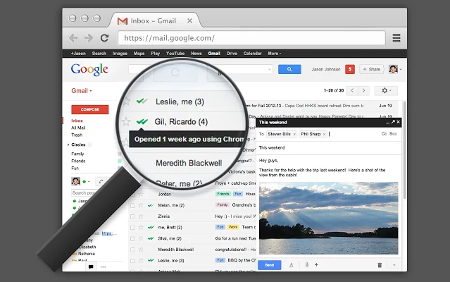
MailTrack has two primary features, which are:
- You’ll be able to see which messages have been read, how long ago, how many times and which device they were opened on.
- You’ll be able to access a dashboard showing you which messages haven’t been read yet.
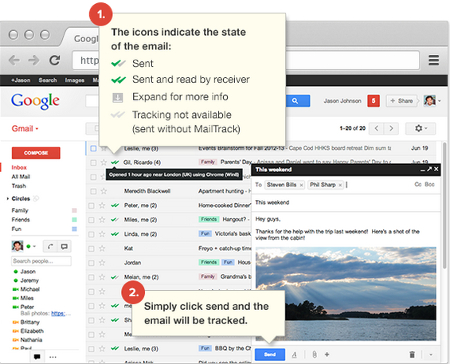
One great thing about MailTrack is how easy it is to use. To find out the status of your sent message, all you have to do is look to the left of its subject line where you will see two check-marks. When both checkmarks become green, it means that the message has been “sent and read by receiver.”
As is the custom with just about every free app or extension, Mailtrack offers a premium version for a monthly fee. The paid version of MailTrack includes these features:
- Daily reports
- Link tracking
- No signature
- Optional tracking
- Unlimited tracking history
Features like these may not appeal to a casual Gmail user who only wishes to use MailTrack to know if their message has been read or not, but the paid version is worth considering if you’re a heavy email user and see value to it.
In addition to easing your email stress levels, email-tracking applications like MailTrack have a practical use for your office: keeping workers accountable to read each other’s messages. Using an app like MailTrack will remove the age-old excuse, “Looks like I didn’t get your message. Try sending it again.” With MailTrack, you’ll be able to call out a bluff like this by saying, “Oh yeah? Well, I see two green checkmarks that say otherwise.”
Apps like MailTrack help make your office more productive. To discover additional time-saving technologies for your workplace, give Voyage Technology a call at 800.618.9844, and be sure to subscribe to our blog for a new tip every week.


