 Most computer users should practice the policy of ensuring optimal security on their PCs. To this end, assuming that you’ll be hacked (or at least targeted) at some point is pretty reasonable, as it allows you to plan ahead and take preventative actions. Still, there are plenty of people in the world who don’t care enough or worry enough to make security-minded decisions. Contrary to popular belief, there are countless ways that a hacker can take advantage of a hacked PC.
Most computer users should practice the policy of ensuring optimal security on their PCs. To this end, assuming that you’ll be hacked (or at least targeted) at some point is pretty reasonable, as it allows you to plan ahead and take preventative actions. Still, there are plenty of people in the world who don’t care enough or worry enough to make security-minded decisions. Contrary to popular belief, there are countless ways that a hacker can take advantage of a hacked PC.
Any business owner who considers security a top priority clearly understands this, but those who don’t, who think that they’re impervious to hacking attacks, are in for a rude awakening. Hackers understand how important data is, and they’ll do everything they can to take your precious information for themselves. The smart business owner realizes that hackers have found ways to monetize just about all types of data that can be found on a computer, so it’s simply a matter of time before hackers realize just how valuable your business in particular is for their purposes.
Even data that’s seemingly simple and benign presents some kind of value on the online black market. In terms of the general availability of valuable data, even the most civilianized PC can potentially be a goldmine for hackers. An infected PC can yield untold amounts of possibilities. Hackers can turn your PC into a spambot, rig it to collect information with spyware and trojans, and use it to spread threats as part of a botnet.
To emphasize just how dangerous an infected PC can be, check out this infographic used by Brian Krebs on his security website:
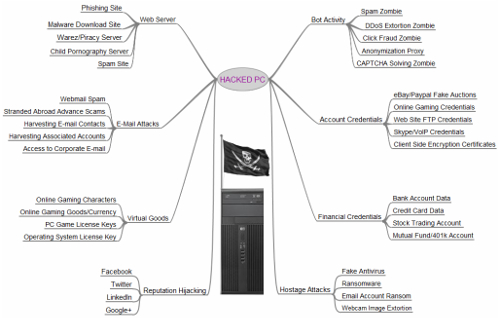
As displayed, hackers have no shortage of possibilities with the average user’s PC. The unfortunate truth is that no matter what your PC or workstation is being used for, a hacker has a use for it, too, and will use whatever means at their disposal to leverage it to their benefit. For example, a computer could hold sensitive credentials stored in the web browser, or it could find personal information stored away in long-forgotten files. The average cost of a data breach per lost or stolen record is $154, so if you have a few hundred or a few thousand contact records, you need to ask yourself if your business can risk such a ridiculous mistake.
Especially in a business environment, you need to be very careful navigating online, and you should be taking advantage of proactive security solutions designed to minimize risk. The idea behind these proactive measures is that your organization can catch small issues and resolve them before they become large problems that are difficult to contain.
A Unified Threat Management (UTM) solution is a great tool that can help your business successfully avoid the majority of threats to your IT infrastructure. The UTM makes use of powerful security tools like enterprise-level firewalls and antivirus, and compounds them with preventative tools like web content filtering and spam blocking. By doing so, your workstations and the network they’re connected to can dodge the majority of threats thrown their way. The hard lesson to learn with cybersecurity is that there is no “full” guarantee that you’ll never be targeted, so it’s your responsibility to mitigate potential damage before it’s too late. Hoping for the best isn’t going to stop hackers from accessing your critical business systems.
The best way to approach cyber security for your business is with Voyage Technology by your side. Our trusted technicians can help to pinpoint weak links in your system infrastructure, and how to remedy them with best practices and security solutions. To learn more, give us a call at 800.618.9844.


